Token Security Management
Overview
The Token Security Management module provides unified identity verification and authorization management for system API integration. This module supports API integration through both RSA open tokens and the system's JWT tokens, with RSA tokens being the default; it allows users to create tokens with specific API access permissions for core systems or designated users/projects.
Before You Start
Permission Configuration
To ensure the following operational processes proceed normally, please confirm that you have Project Administrator permissions.
RSA Tokens
RSA Token: An API authentication credential based on asymmetric encryption algorithm, using public key encryption and private key decryption mechanism to ensure data transmission security.
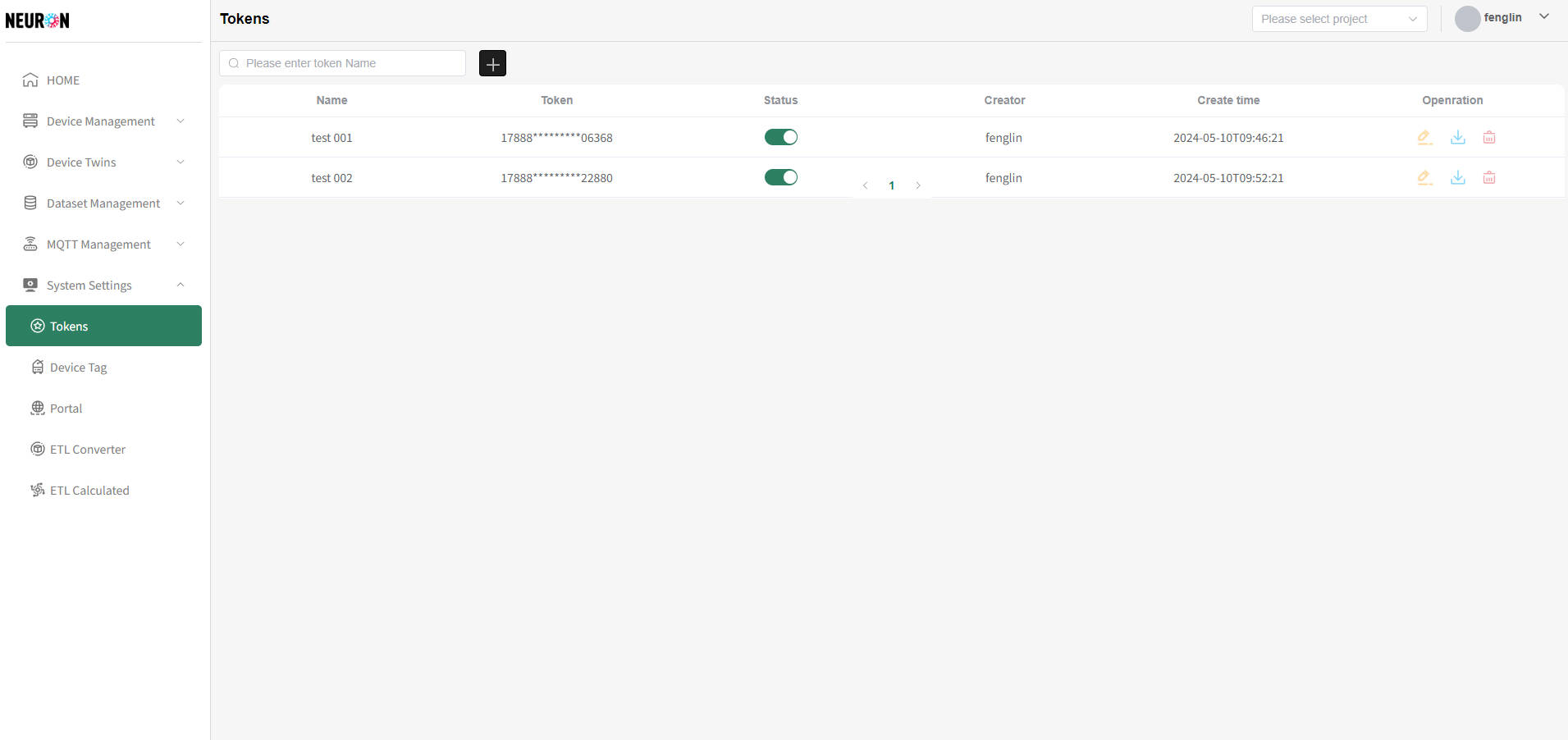
RSA Token List
All tokens displayed in the token list have been successfully applied for. You can download and view token file information as needed, and also modify current token information.
The system supports fuzzy matching queries for token names.
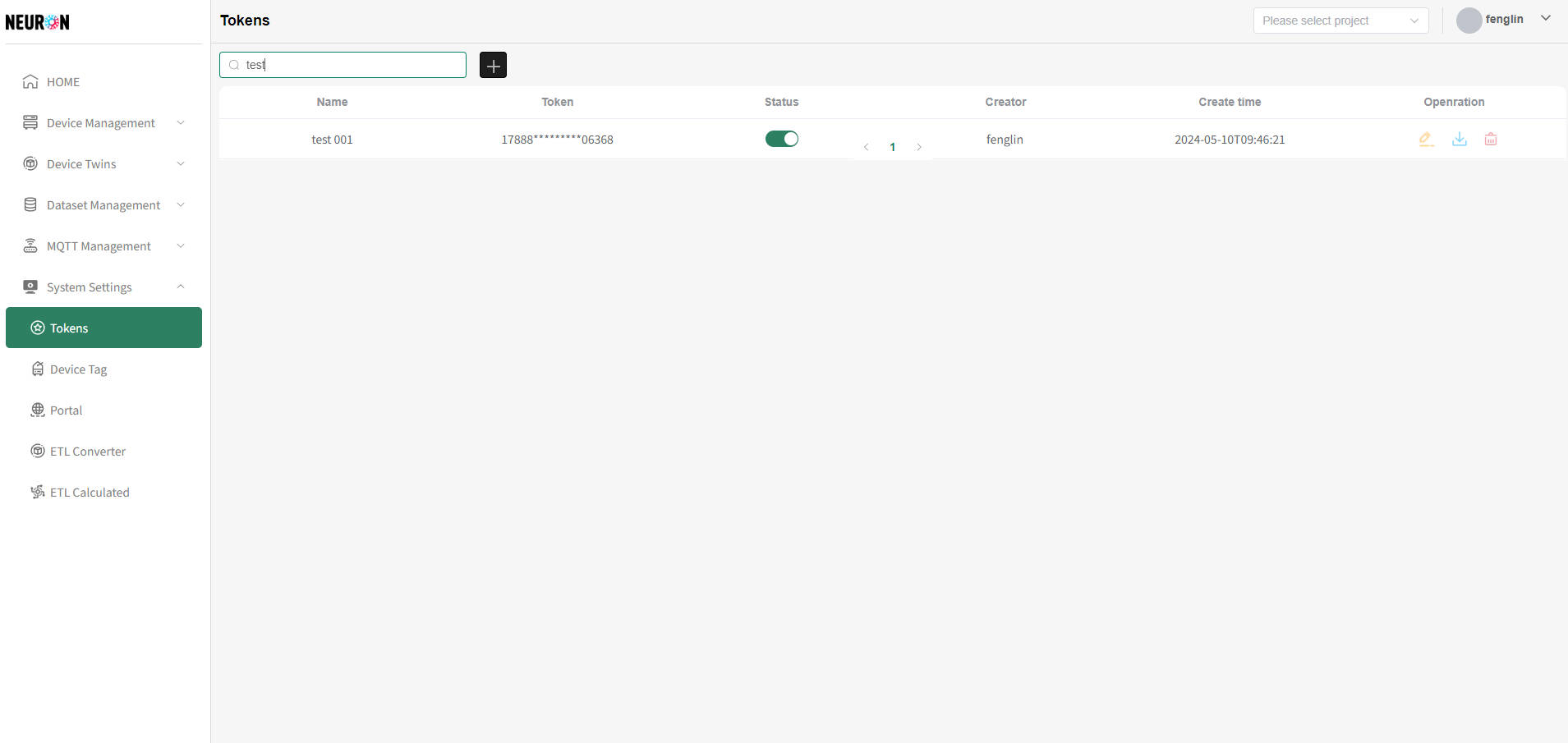
 As shown below, enter information in the input box and press Enter to refresh the device list.
As shown below, enter information in the input box and press Enter to refresh the device list.
RSA Token Application
 As shown above, on the token list page, click the "+" button to apply for a new token, as shown below.
As shown above, on the token list page, click the "+" button to apply for a new token, as shown below.
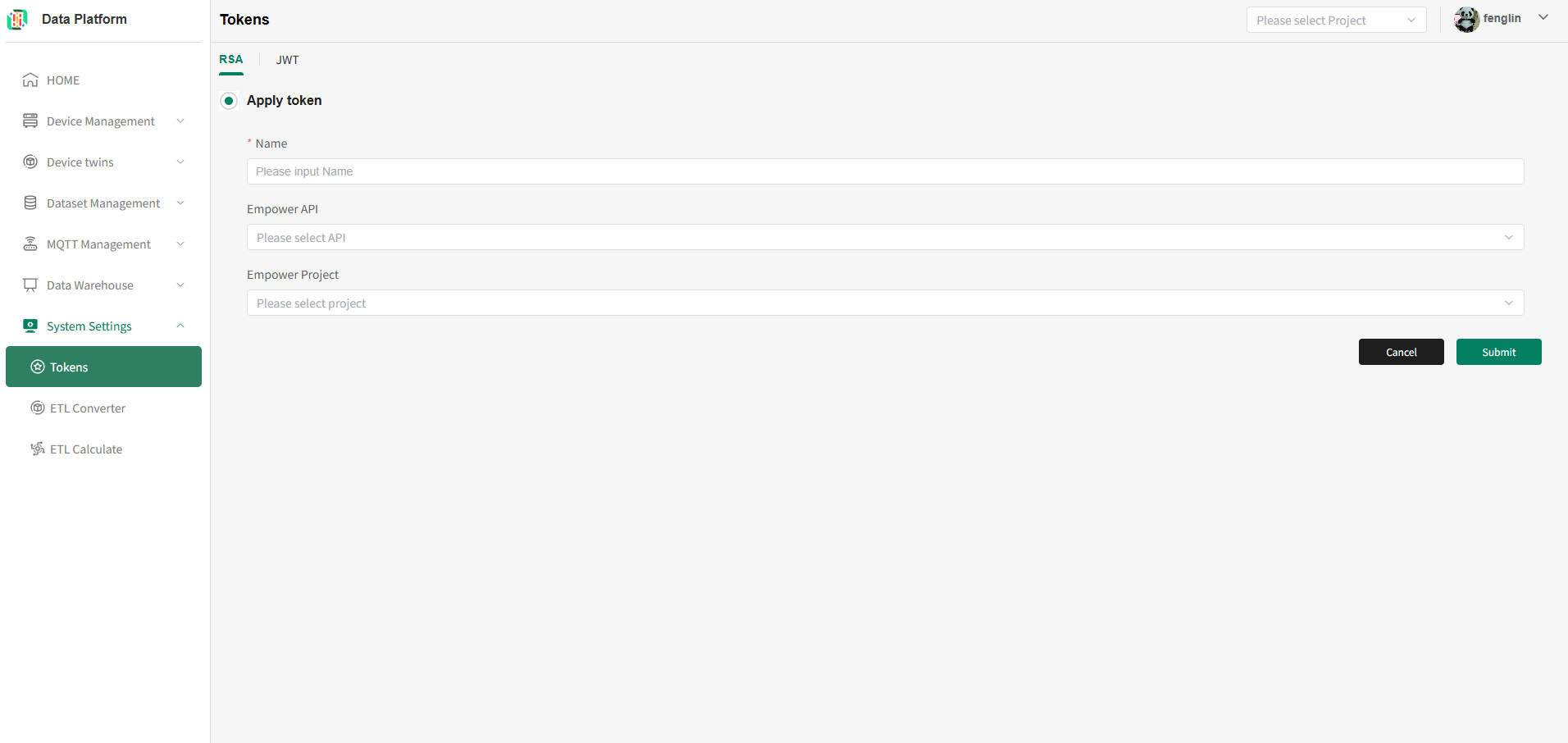
Description of the above figure:
- Fill in the token name [Globally unique];
- Check the authorized APIs [Multiple selection allowed];
- Check the authorized platform projects [Multiple selection allowed].
As shown above, enter the corresponding information. After clicking submit, the system will issue the token, as shown below.
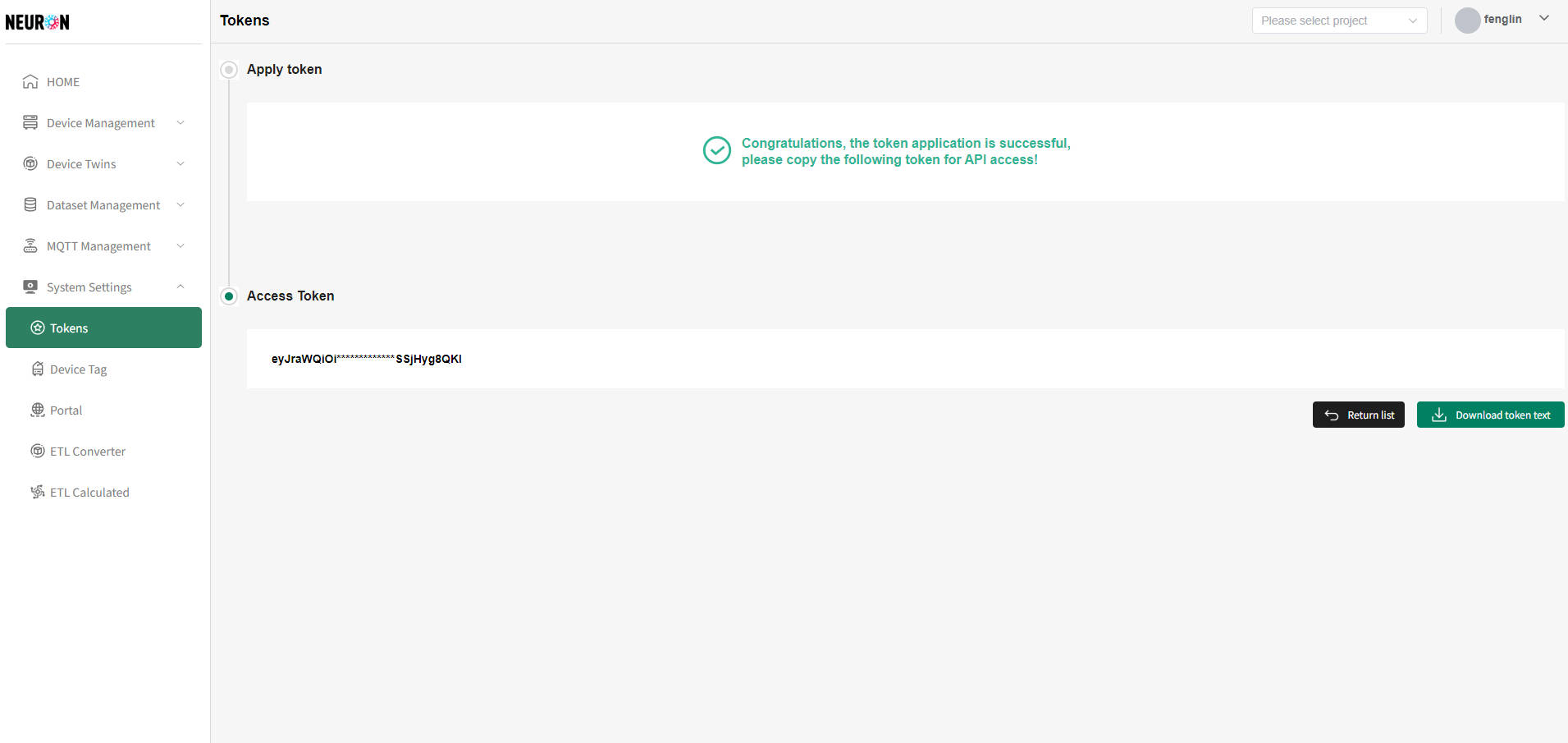 As shown above, click "Return List" to return to the token list, click "Download token test" to download the current token information.
As shown above, click "Return List" to return to the token list, click "Download token test" to download the current token information.
RSA Token Download
- Download from Token List Page
On the token list page, you can click the "Download" button in the operation column on the right side of the token to be downloaded to directly download the current token's information, as shown below.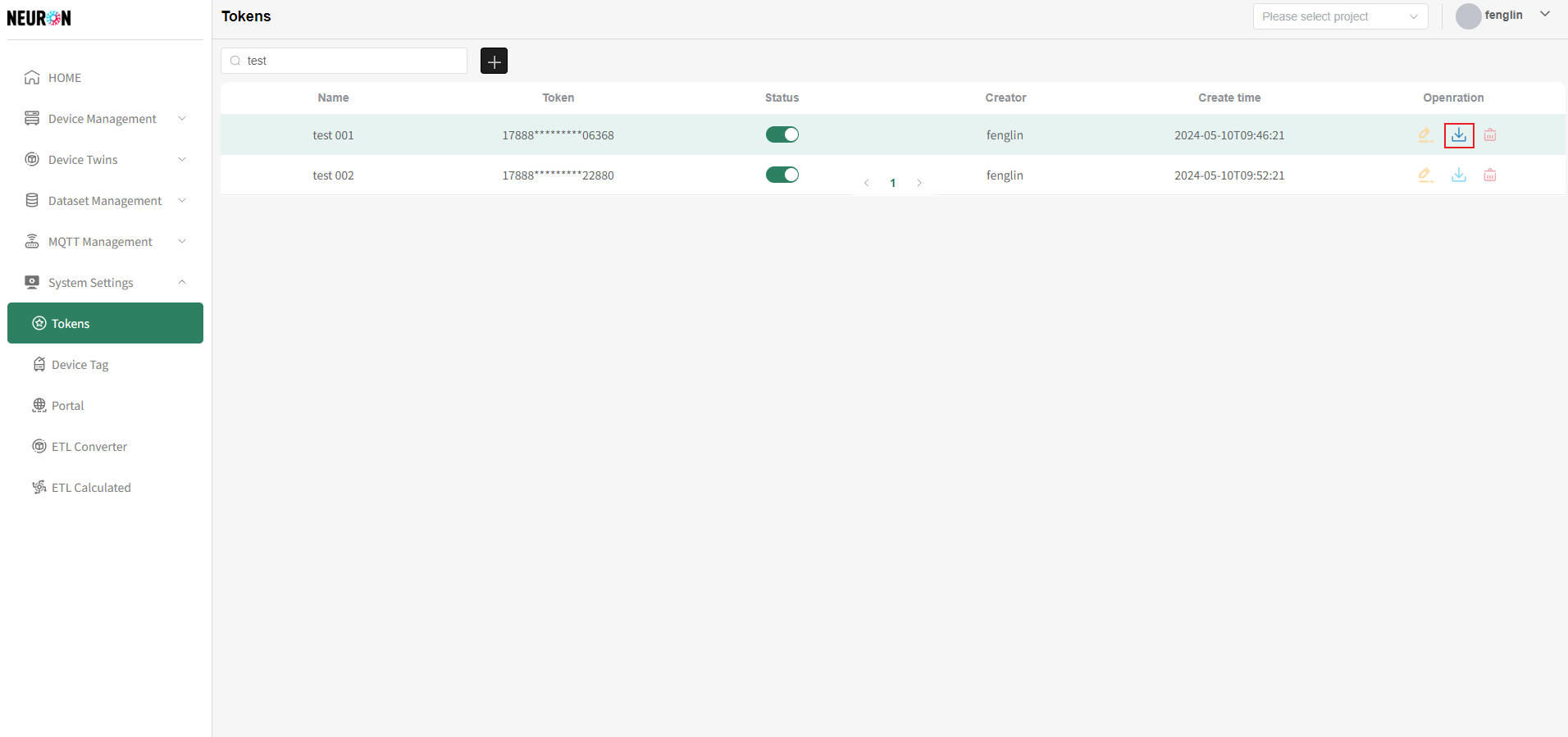
- Download during Application or Modification
On the successful token application or modification page, you can click the "Download" button to download the current token's information, as shown below.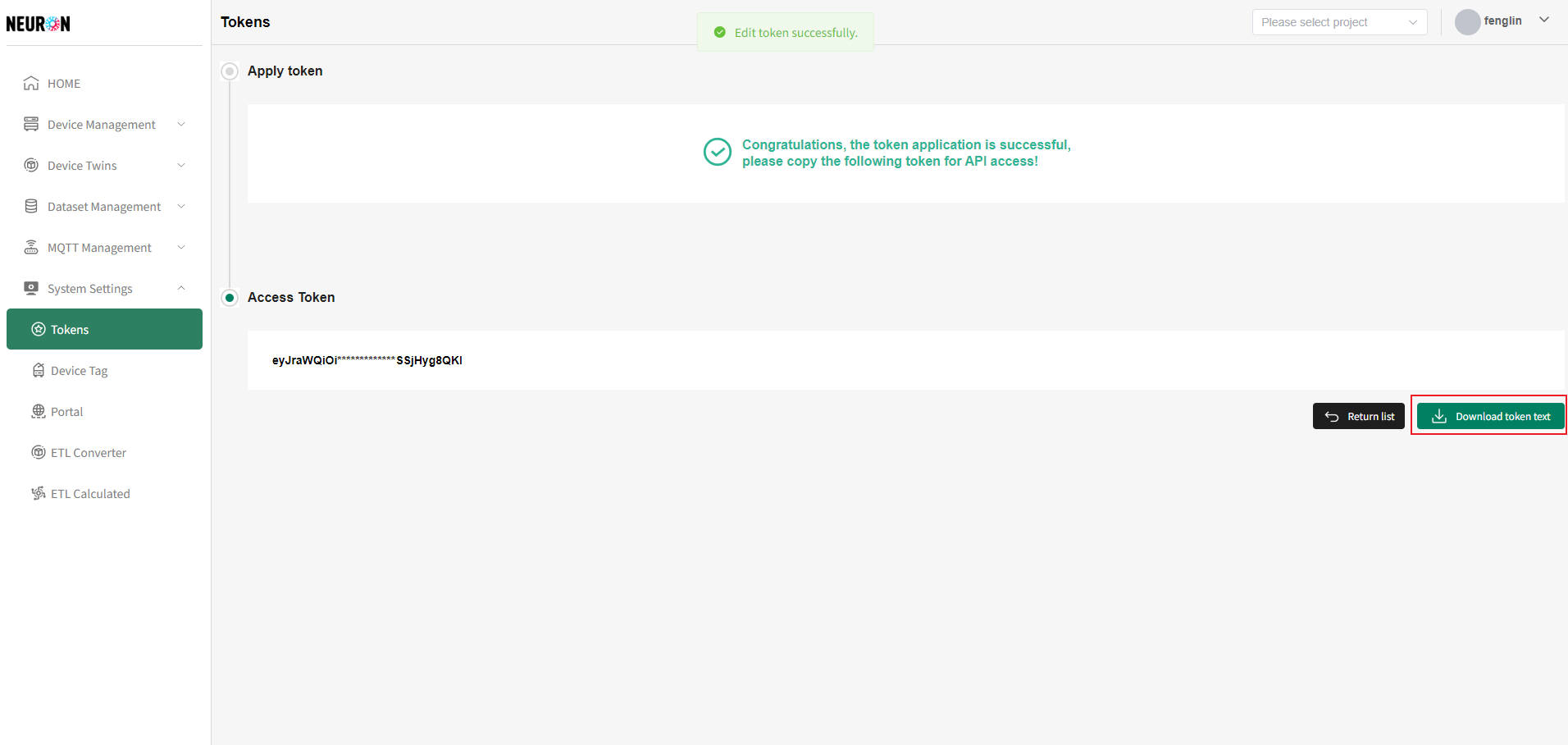
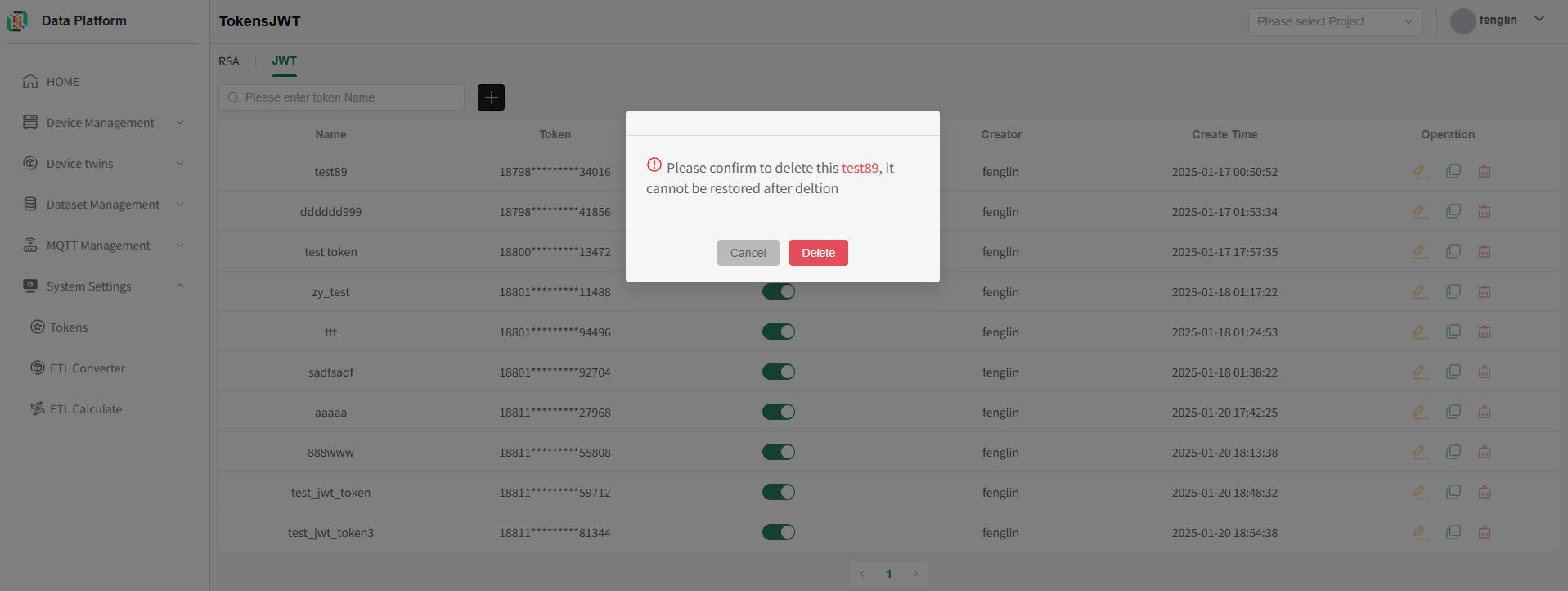
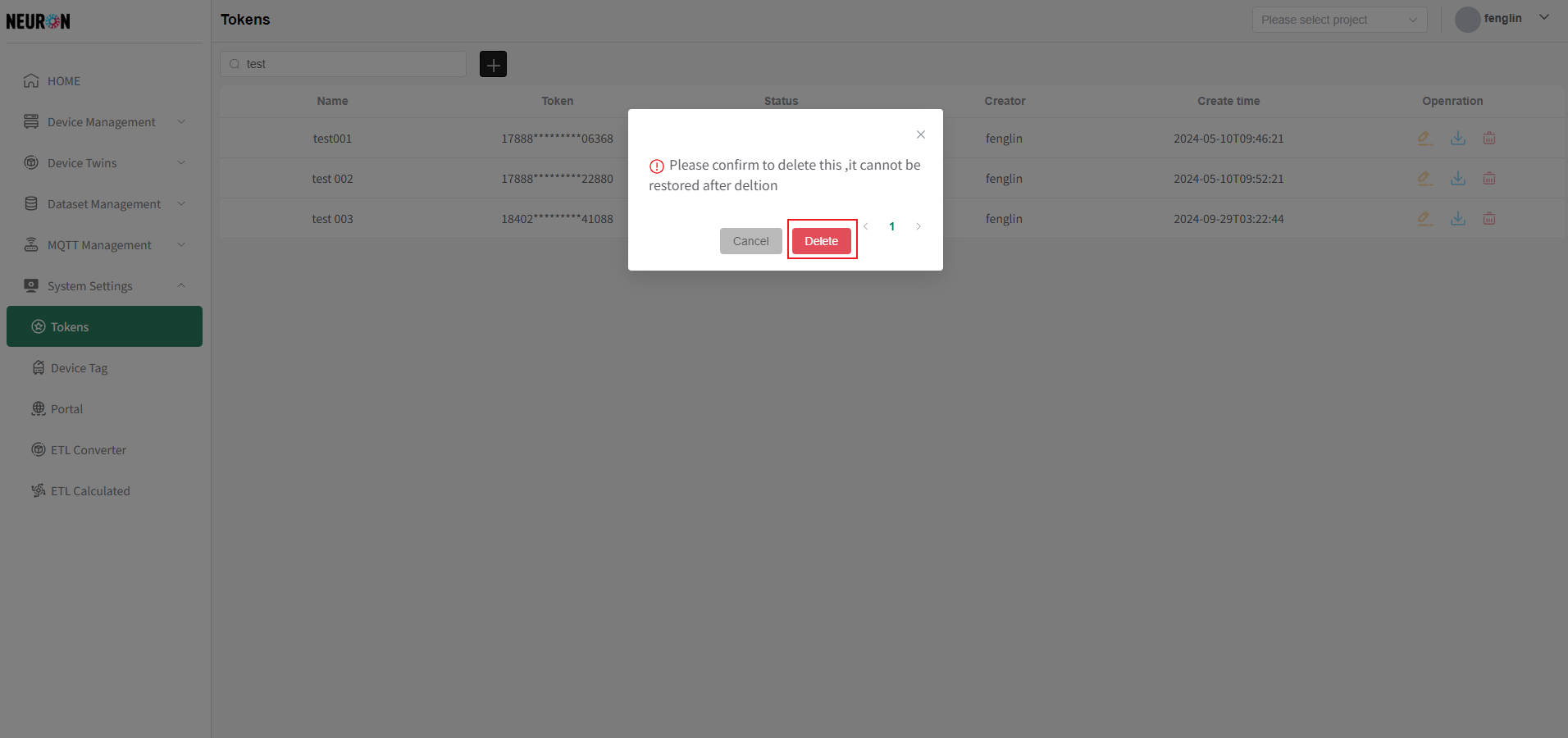
RSA Token Deletion
Token deletion should be done with caution. Once deleted by the system, it cannot be recovered. If a token used in the API is deleted, it will cause token verification to fail. It can only function normally after modification.
On the token list page, you can click the "Delete" button in the operation column on the right side of the token to be deleted, as shown below.
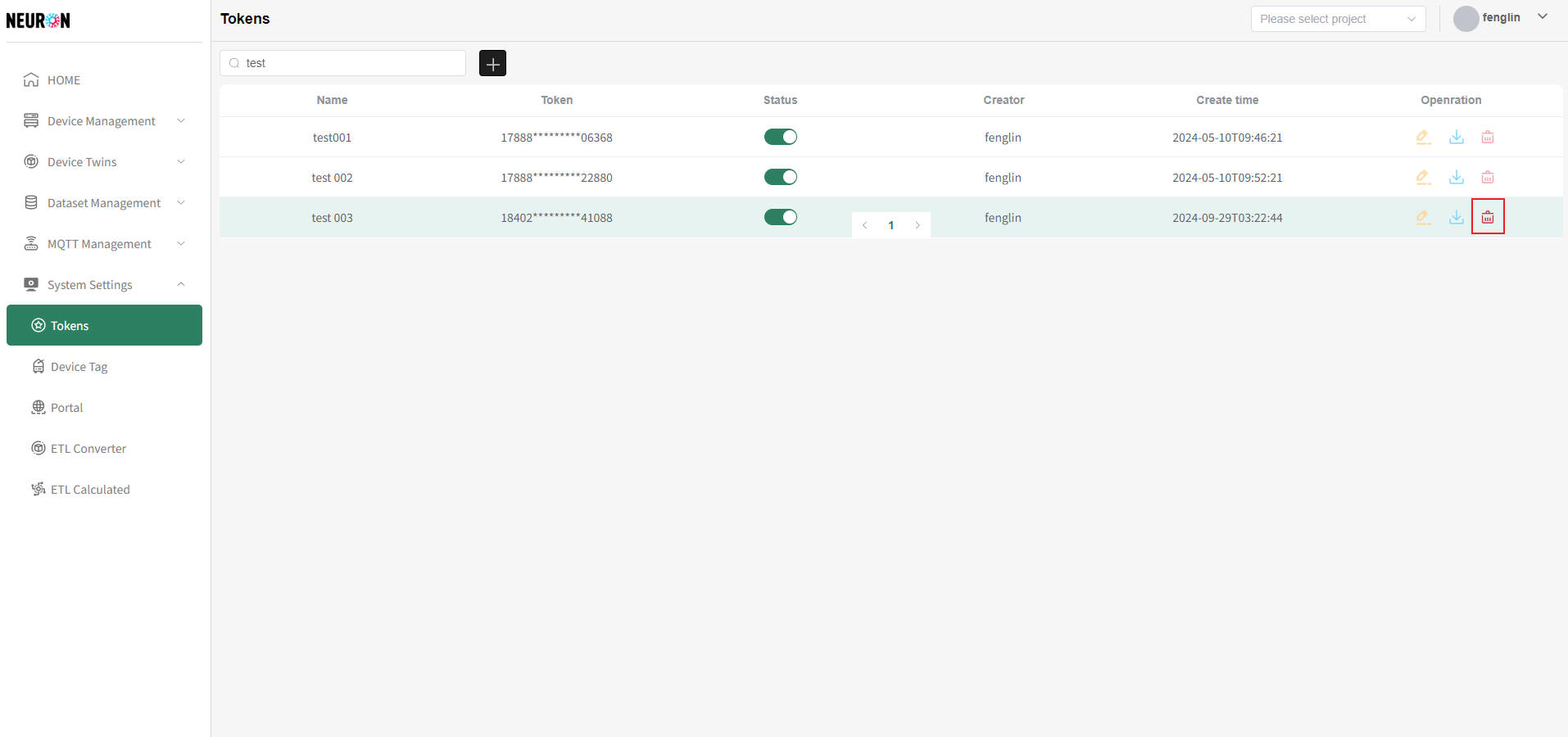 As shown above, click "Delete" in the confirmation box to directly delete the token irrecoverably, as shown below.
As shown above, click "Delete" in the confirmation box to directly delete the token irrecoverably, as shown below.
JWT Tokens
JWT Token: A JSON-based open standard token that uses digital signatures to ensure token integrity and trustworthiness.
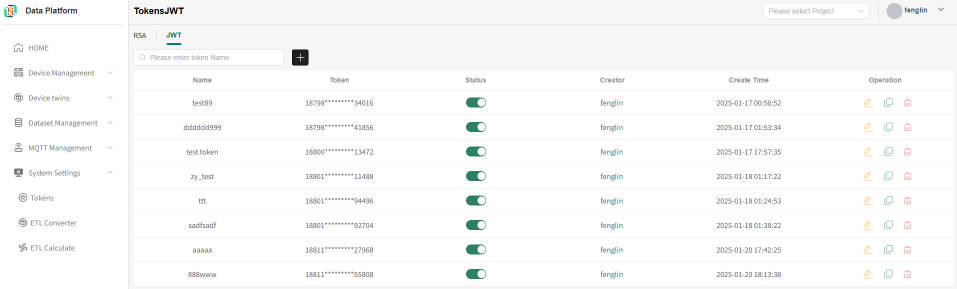
JWT Token List
Switch the type to JWT. Tokens displayed in the token list are successfully applied JWT tokens. Token file information can be downloaded and viewed as needed, and current token information can also be modified.
The system supports fuzzy matching queries by token name.
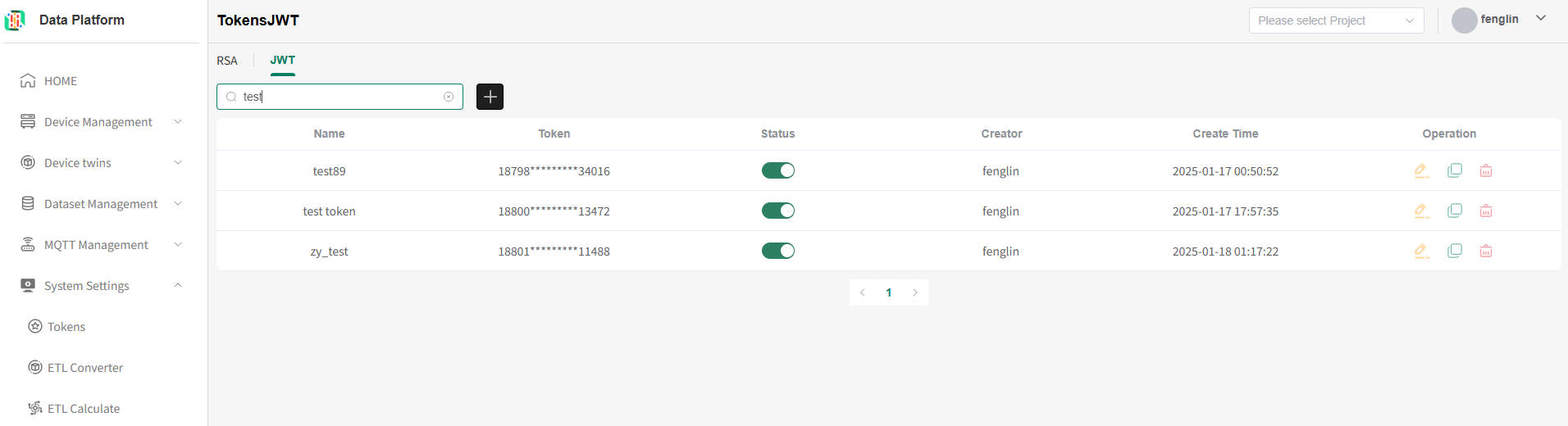
 As shown below, enter information in the input box and press Enter to refresh the device list.
As shown below, enter information in the input box and press Enter to refresh the device list.
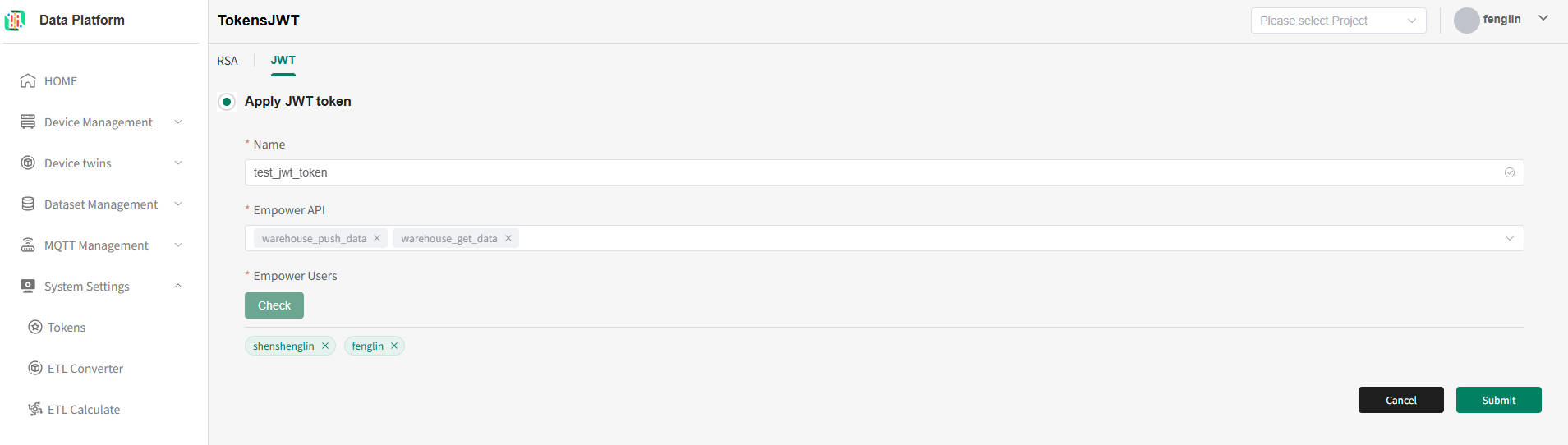
JWT Token Application
 As shown above, on the token list page, click the "+" button to apply for a new token, as shown below.
As shown above, on the token list page, click the "+" button to apply for a new token, as shown below.
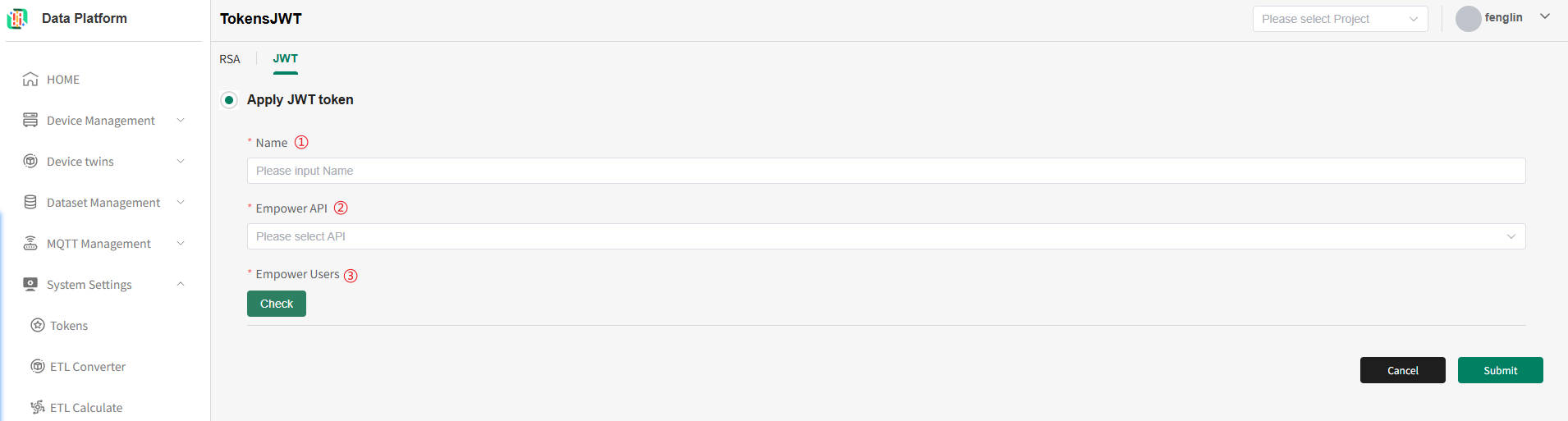
Description of the above figure:
- Fill in the token name [Globally unique];
- Check the authorized APIs [Multiple selection allowed];
- Check the authorized users [Multiple selection allowed].
As shown above, after entering the corresponding information, click submit. The system will issue the token, as shown below.
 As shown above, click "Return List" to return to the token list, click "Copy secret id" to copy the current token information.
As shown above, click "Return List" to return to the token list, click "Copy secret id" to copy the current token information.
JWT Secret Id Copy
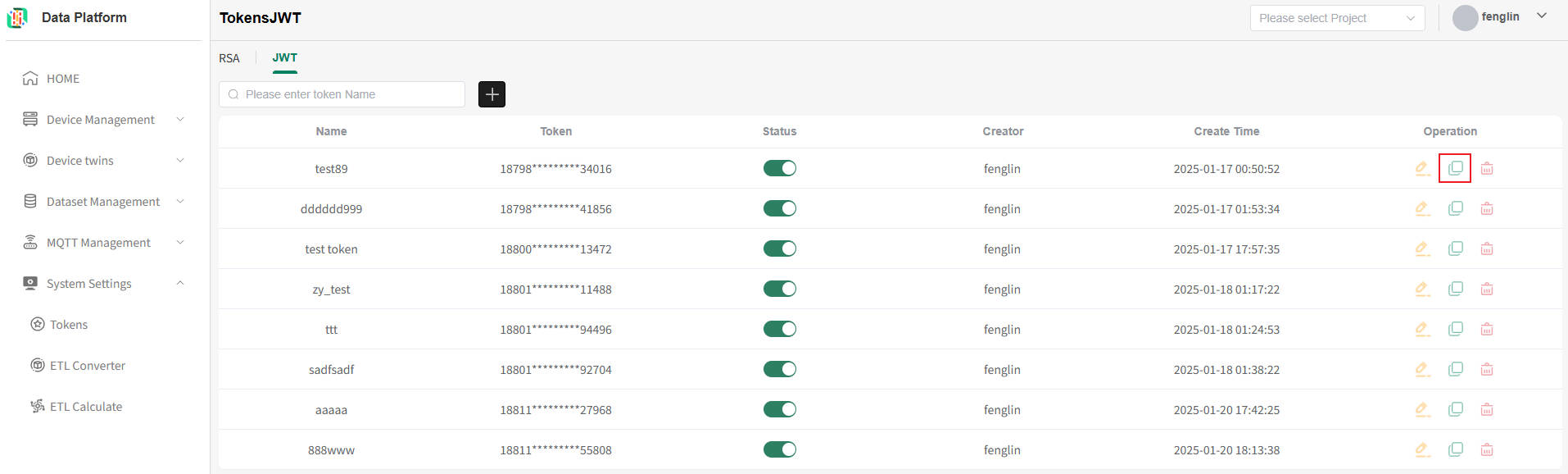
- Copy from Token List Page
On the token list page, you can click the "Copy" button in the operation column on the right side of the token to be copied to directly copy the current token's information, as shown below.
- Copy during Application or Modification
On the successful token application or modification page, you can click the "Copy secret id" button to copy the current token's information, as shown below.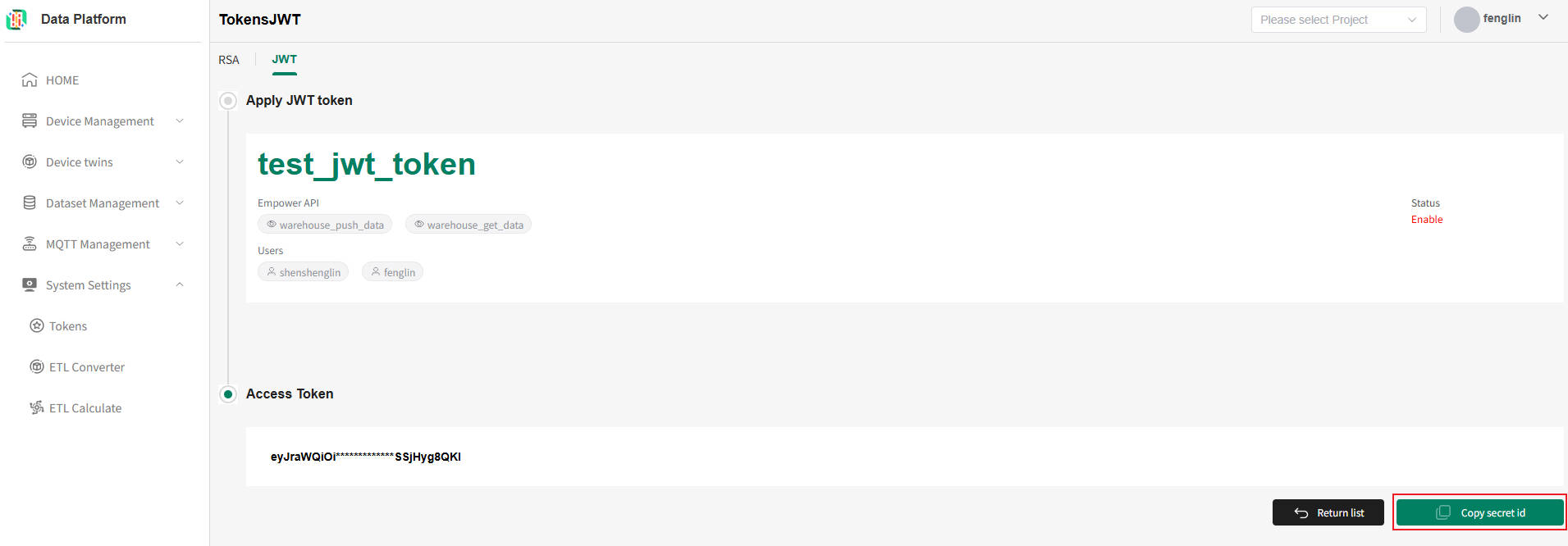
JWT Token Deletion
Token deletion should be done with caution. Once deleted by the system, it cannot be recovered. If a token used in the API is deleted, it will cause token verification to fail. It can only function normally after modification.
On the token list page, you can click the "Delete" button in the operation column on the right side of the token to be deleted, as shown below.
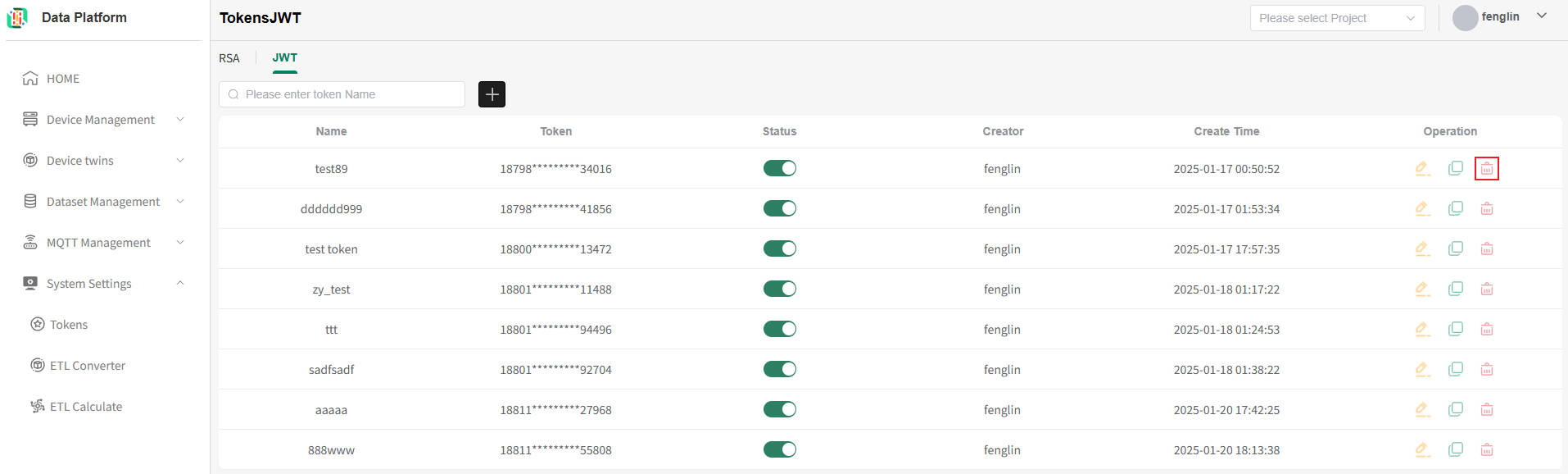 As shown above, click "Delete" in the confirmation box to directly delete the token irrecoverably, as shown below.
As shown above, click "Delete" in the confirmation box to directly delete the token irrecoverably, as shown below.